
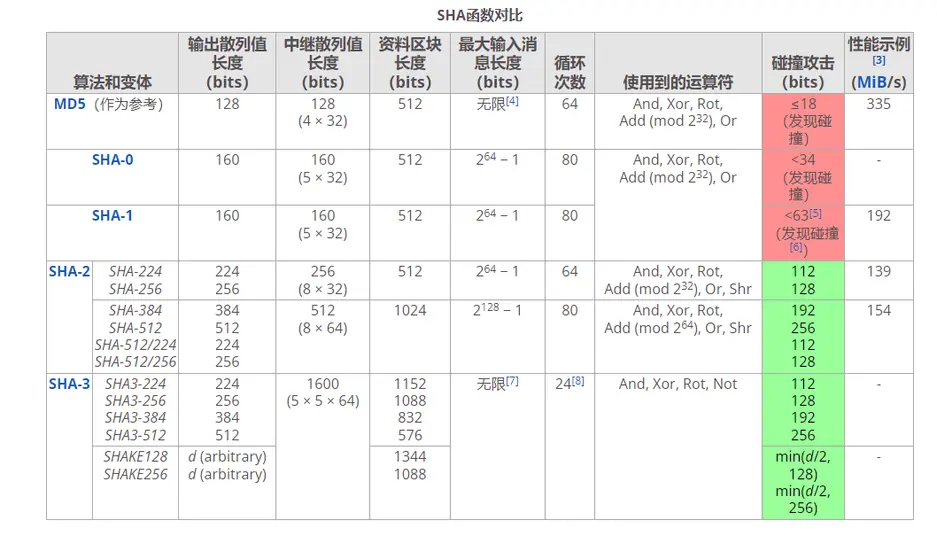
每种哈希函数的特征
1.MD5
初始化魔数:
A = 0x67452301;
B = 0xEFCDAB89;
C = 0x98BADCFE;
D = 0x10325476;
K表
K1 = 0xd76aa478
K2 = 0xe8c7b756
K3 = 0x242070db
K表来自sin函数
输出长度16个字节,或者说32个十六进制数,有时候输出16个十六进制数。
2.SHA1
A = 0x67452301
B = 0xEFCDAB89
C = 0x98BADCFE
D = 0x10325476
E = 0xC3D2E1F0
和MD5相比,有五个初始化链接变量,而且前四个链接变量完全相同。
输出长度20个字节,或者说40个十六进制数。
只有四个K值,每20轮用同一个K作变换
K1 = 0x5a827999
K2 = 0x6ed9eba1
K3 = 0x8f1bbcdc
K4 = 0xca62c1d6
3.SHA256
A = 0x6A09E667;
B = 0xBB67AE85;
C = 0x3C6EF372;
D = 0xA54FF53A;
E = 0x510E527F;
F = 0x9B05688C;
G = 0x1F83D9AB;
H = 0x5BE0CD19;
八个初始化链接变量
输出长度为32个字节,或者说64个十六进制数
有64个K值,每轮1个K值
K1 = 0x428a2f98
K2 = 0x71374491
K3 = 0xb5c0fbcf
K4 = 0xe9b5dba5
K值来自素数
4.SHA 512
A = 0x6a09e667f3bcc908;
B = 0xbb67ae8584caa73b;
C = 0x3c6ef372fe94f82b;
D = 0xa54ff53a5f1d36f1;
E = 0x510e527fade682d1;
F = 0x9b05688c2b3e6c1f;
G = 0x1f83d9abfb41bd6b;
H = 0x5be0cd19137e2179;
八个初始化链接变量,IDA反编译也时常显示为16个。
输出长度为64字节,或者说128个十六进制数
有80个K,每一轮一个K,K值来自素数。
K1 = 0x428a2f98d728ae22
K2 = 0x7137449123ef65cd
K3 = 0xb5c0fbcfec4d3b2f
K4 = 0xe9b5dba58189dbbc
和SHA256的K有关联。
HMAC
HMAC-MD5
HMAC-SHA1
HMAX-XXX 加盐+双重哈希方案
HMAC MD5
Cyberchef
HMAC-MD5
明文:123456(utf-8)
密文:111111(utf-8)
结果:5542af910b1ff3f554dcdfb7ceccebc8
公式:

第一步(让密钥的长度达到分组长度):
如果密钥长度超过512bit,先进行一次MD5后:16个字节+00000…
k = 0x313131313131
密钥进行扩展
MD5: 512比特–64字节–128hex 分组长度
(十六进制,128长度)
k’=0x31313131313100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
第二步(k’⊕opad):
先对opad填充到分组长度
0x5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c
进行异或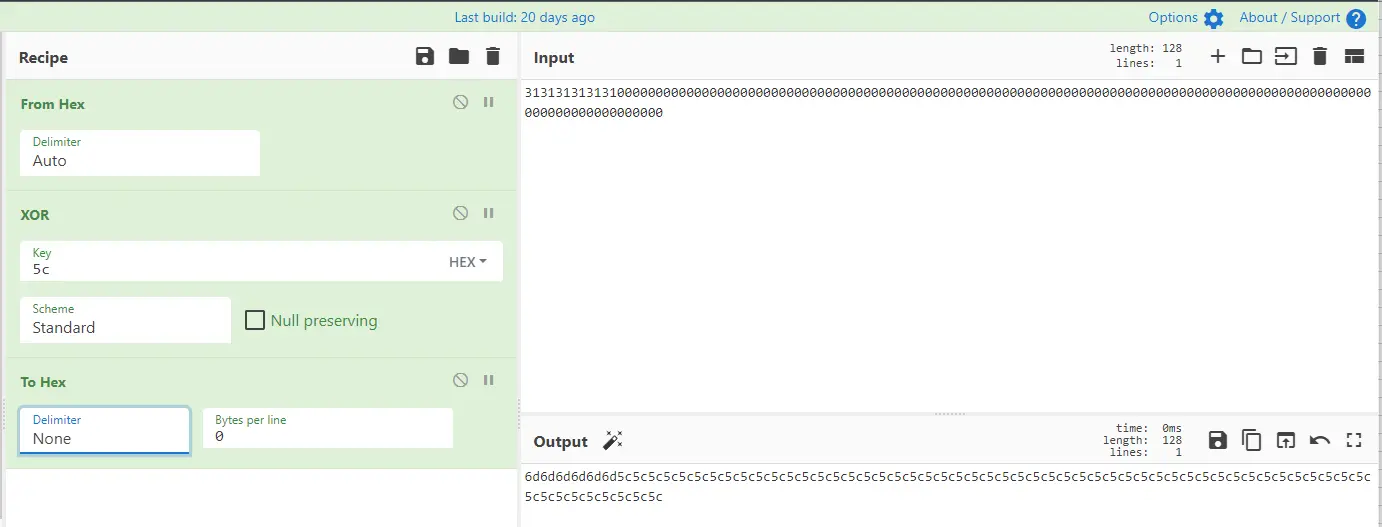
k’⊕opad=0x6d6d6d6d6d6d5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c
第三步(k’⊕ipad):
先对ipad填充到分组长度
0x36363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636
进行异或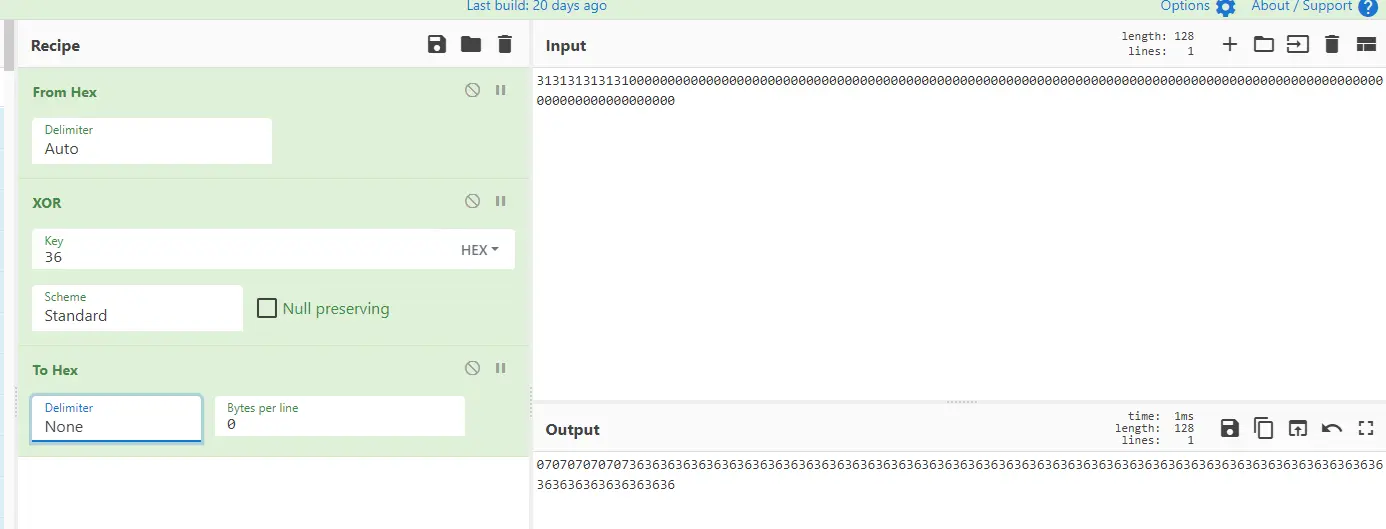
k’⊕ipad=0x07070707070736363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636
第四步级联明文((k’⊕ipad)||m):
(k’⊕ipad)||m=0x07070707070736363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636313233343536
第五步级联后进行md5(H((k’⊕ipad)||m)):
级联后进行一次md5(不需要转hex)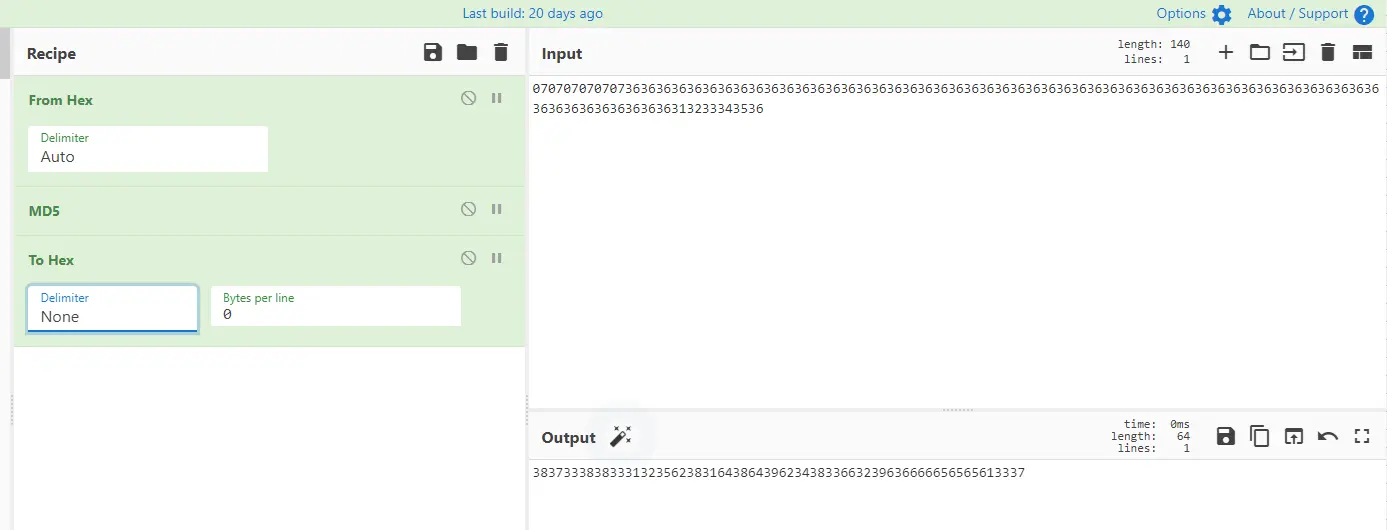
H((k’⊕ipad)||m)=873883125b81d8d9b483f29cffeeea37
第六步(第二步级联第五步后进行md5,H((k’⊕opad)||H((k’⊕ipad)||m))
0x6d6d6d6d6d6d5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c873883125b81d8d9b483f29cffeeea37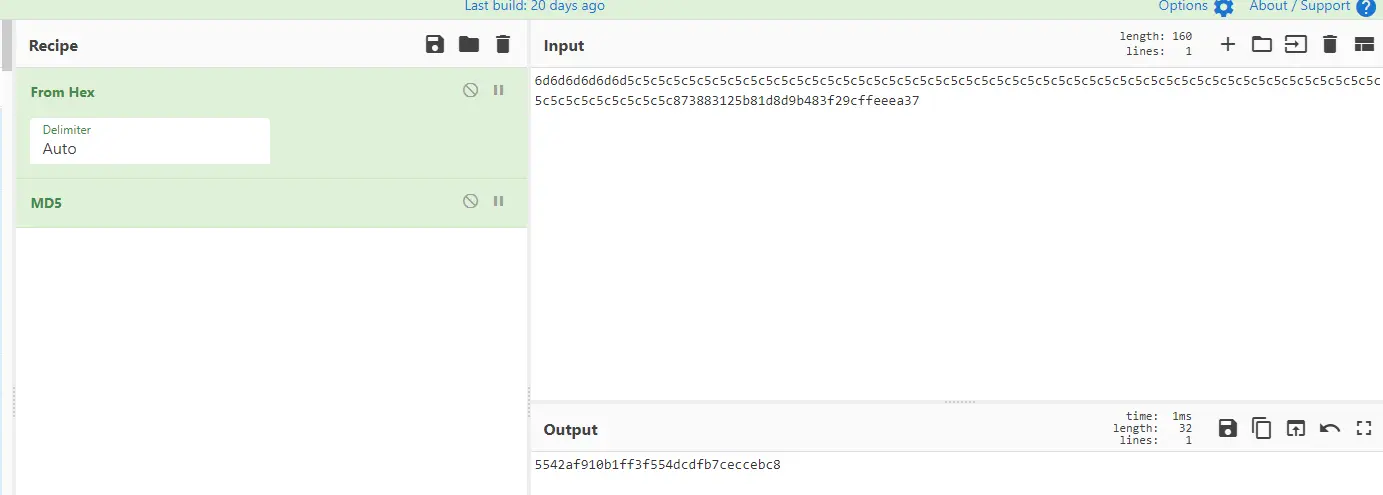
结果:5542af910b1ff3f554dcdfb7ceccebc8
结果跟Cyberchef的HMAC-MD5一致
HMAC SHA1
Cyberchef
HMAC-SHA1
明文:helloword(utf-8)
密文:1111(hex)
结果:4ea30551db501b285a03a197c65fea249131b808
第一步(让密钥的长度达到分组长度):
如果密钥长度超过512bit,先进行一次SHA1后:16个字节+00000…
k = 0x1111
密钥进行扩展
SHA1: 512比特–64字节–128hex 分组长度
(十六进制,128长度)
k’=0x11110000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
第二步(k’⊕opad):
异或0x5c
先对opad填充到分组长度
0x5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c
然后进行异或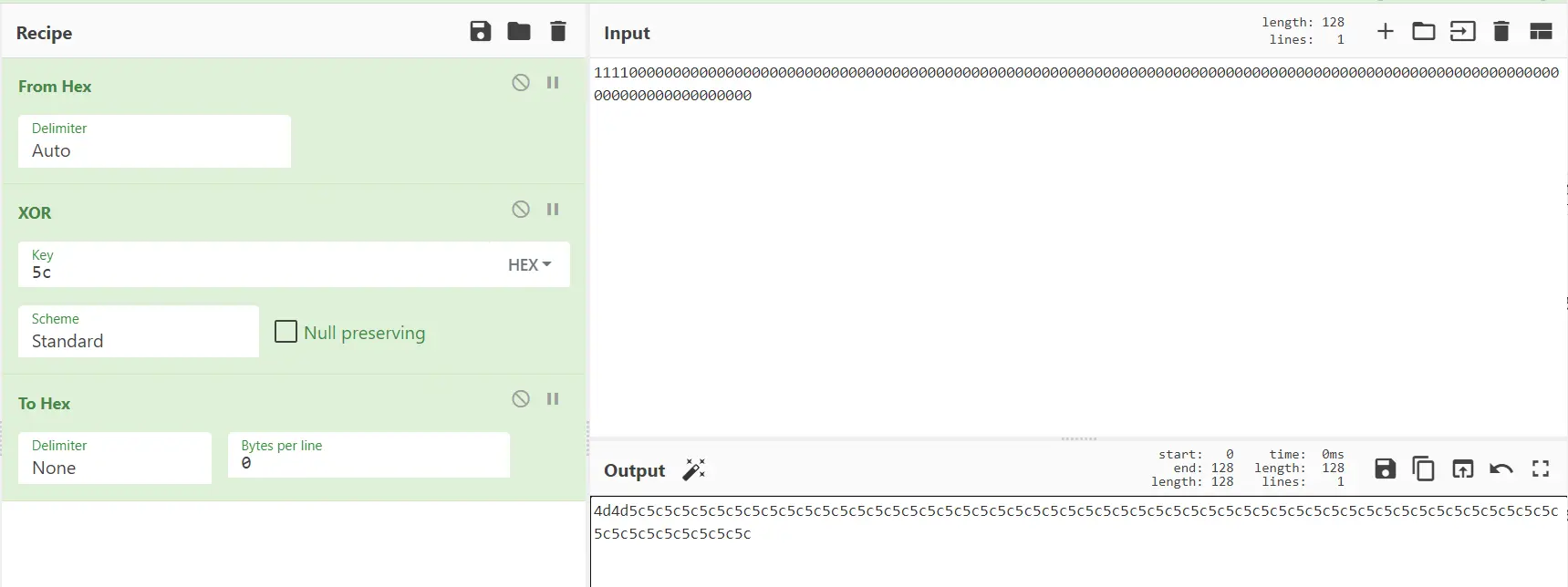
k’⊕opad=0x4d4d5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c
第三步(k’⊕ipad):
异或0x36
先对ipad填充到分组长度
0x3636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636
进行异或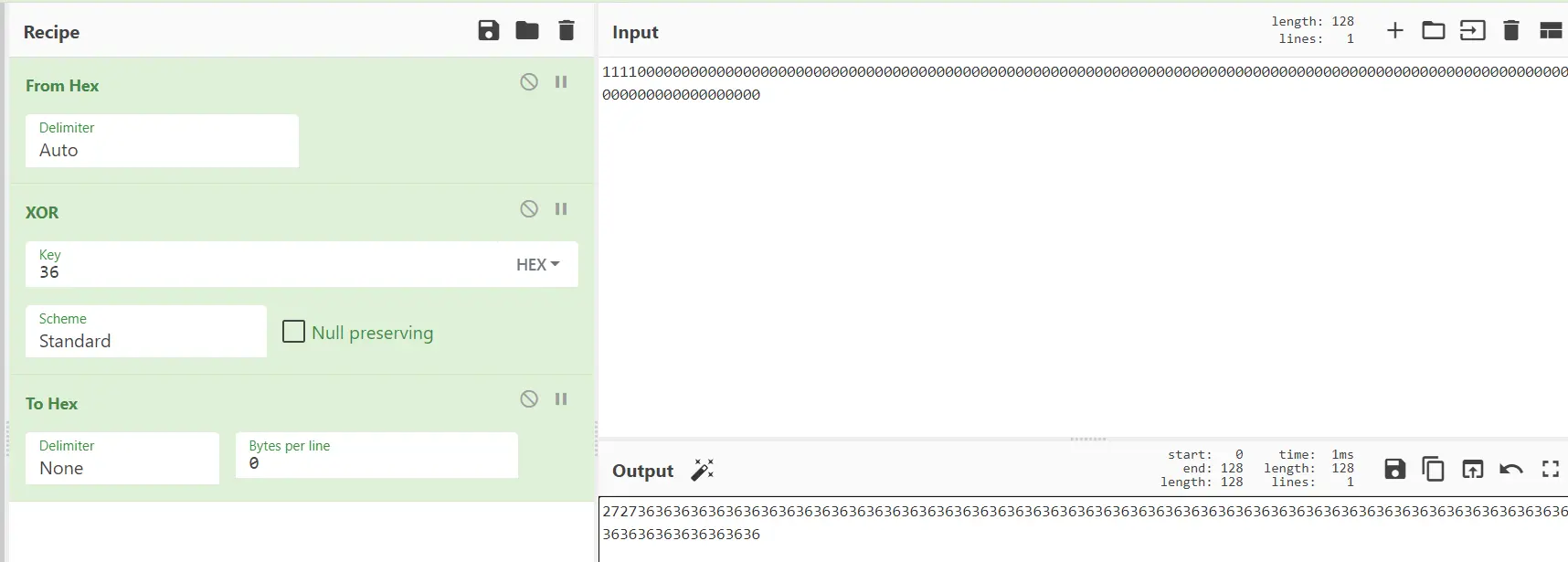
k’⊕ipad=0x27273636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636
第四步级联明文((k’⊕ipad)||m):
(k’⊕ipad)||m=0x2727363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363636363668656c6c6f776f7264
第五步级联后进行sha1(H((k’⊕ipad)||m)):
级联后进行一次sha1(不需要转hex)
H((k’⊕ipad)||m)=aea39b30d6922fdbb1848fe3a49bd130ed337f77
第六步(第二步级联第五步后进行sha1,H((k’⊕opad)||H((k’⊕ipad)||m))
级联(k’⊕opad)||H((k’⊕ipad)||m)=0x4d4d5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5c5caea39b30d6922fdbb1848fe3a49bd130ed337f77
4ea30551db501b285a03a197c65fea249131b808
总结
第一步k值填充到块长度(md5和sha1是512bit,128hex)称为k’
第二步k’与0x36异或后拼接明文的hex,进行原函数哈希(如hmac md5就进行一次md5,hmac sha1就进行一次sha1)
第三步k’与0x5c异或后拼接第二步再进行一次原函数哈希
